Finally, final version of TLS 1.3 has now been published as of August 2018.
TLS 1.3 in 2018, encrypted connections are now more secure and faster than ever.
What is TLS?
TLS stands for Transport Layer Security and is the successor to SSL (Secure Sockets Layer). TLS provides secure communication between web browsers and servers. The connection itself is secure because symmetric cryptography is used to encrypt the data transmitted. The keys are uniquely generated for each connection and are based on a shared secret negotiated at the beginning of the session, also known as a TLS handshake.
Updated April 29, 2019
Who providing DNS-over-TLS service?
1. Quad9
2. Cloudflare
3. Dnsprivacy.org public test servers ( blahdns.com )
Who using DNS-over-TLS?
1. Router
2. Stubby
3. Unbound
4. Knot-resolver
5. Android 9 PIE
6. Linux
Below is a demo how I migrate from knot-resolver TLS to haproxy TLS to support TLS 1.3
// ENV, Debian9, with certbot, knot-resolver, haproxy ready
// certbot standalone cert
$ certbot certonly --standalone -d dns.jp.blahdns.com --non-interactive --agree-tos --email [email protected]
// Merge fullchain & privkey into one file
$ cat /etc/letsencrypt/archive/dns.jp.blahdns.com/fullchain1.pem /etc/letsencrypt/archive/dns.jp.blahdns.com/privkey1.pem > /etc/haproxy/dns.jp.blahdns.pem
// Install gcc, make, etc. component
$ apt install build-essential libpcre2-dev zlib1g-dev
// Install openssl 1.1.1
$ wget https://www.openssl.org/source/openssl-1.1.1.tar.gz
$ tar -xzf openssl-1.1.1.tar.gz
$ cd openssl-1.1.1
$ ./config --prefix=/opt/openssl-1.1.1 shared
$ make && make install
// haproxy.cfg sample file
global
log /dev/log local0
chroot /var/lib/haproxy
user haproxy
group haproxy
maxconn 4000
pidfile /var/run/haproxy.pid
tune.ssl.default-dh-param 2048
ssl-default-bind-ciphers TLS13-AES-256-GCM-SHA384:TLS13-AES-128-GCM-SHA256:TLS13-CHACHA20-POLY1305-SHA256:EECDH+AESGCM:EECDH+CHACHA20
ssl-default-bind-options no-sslv3 no-tlsv10 no-tlsv11
# Default SSL material locations
ca-base /etc/ssl/certs
crt-base /etc/ssl/private
defaults
mode http
option dontlognull
option redispatch
option http-server-close
retries 3
maxconn 2000
timeout connect 5s
timeout check 10s
timeout client 20s
timeout server 15s
listen dot-in
bind :::853 v4v6 tfo ssl crt /etc/haproxy/dns.jp.blahdns.pem
mode tcp
server dot-server 127.0.0.1:50Besure your haproxy is support TLSv.13
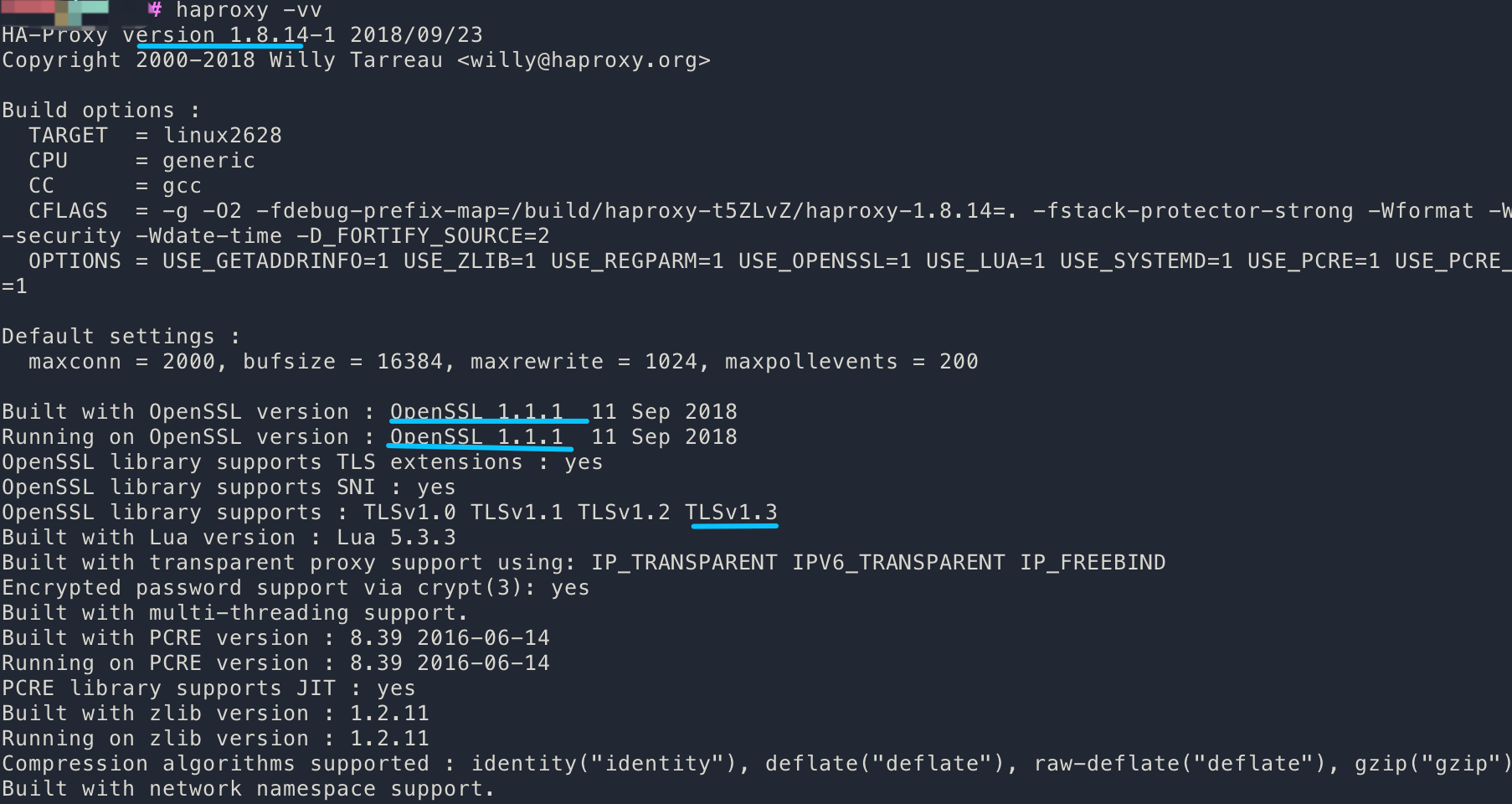
If you want to upgrade to HAProxy 1.9, use this command and update
https://haproxy.debian.net/#?distribution=Debian&release=sid&version=1.9References
1. https://www.cloudflare.com/ssl/encrypted-sni/
2. https://serversforhackers.com/c/letsencrypt-with-haproxy
3. https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Test+Servers
4. https://limbenjamin.com/articles/running-https-ssh-vpn-on-port-443.html
5. https://discourse.haproxy.org/t/tls-termination-proxy-with-both-tls-and-plain-tcp-on-the-same-port/2885/10
6. https://blog.chmd.fr/ssh-over-ssl-episode-4-a-haproxy-based-configuration.html
7. https://github.com/haproxy/haproxy/issues/19 (HAProxy 1.9.x http header example)
